801 | Add to Reading ListSource URL: eoffer.gsa.govLanguage: English - Date: 2014-04-22 14:22:59
|
|---|
802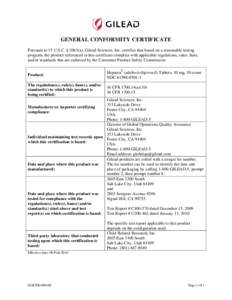 | Add to Reading ListSource URL: www.gilead.comLanguage: English - Date: 2013-02-24 19:40:16
|
|---|
803 | Add to Reading ListSource URL: www2013.wwwconference.orgLanguage: English - Date: 2014-07-21 08:47:06
|
|---|
804 | Add to Reading ListSource URL: graddiv.ucsc.eduLanguage: English - Date: 2014-08-30 22:31:58
|
|---|
805 | Add to Reading ListSource URL: www.landreg.gov.hkLanguage: English - Date: 2015-07-14 05:28:36
|
|---|
806 | Add to Reading ListSource URL: campusorgs.uci.eduLanguage: English - Date: 2015-03-19 12:59:40
|
|---|
807 | Add to Reading ListSource URL: www1.icsi.berkeley.eduLanguage: English - Date: 2012-09-26 16:43:02
|
|---|
808 | Add to Reading ListSource URL: nicca.nic.inLanguage: English - Date: 2014-06-30 05:31:35
|
|---|
809 | Add to Reading ListSource URL: esorics2015.sba-research.orgLanguage: English - Date: 2015-09-22 04:03:47
|
|---|
810 | Add to Reading ListSource URL: digitalpiglet.orgLanguage: English - Date: 2009-11-27 08:33:14
|
|---|